Writing about supply chain disruptions caused by deliberate cyber attacks, Adrian Gonzalez, rhetorically asked, “Is a 9/11-like cyber attack a low probability, high impact supply chain risk?” [“The Next 9/11: The Risk of a Supply Chain Cyberwar,” Logistics Viewpoints, 27 July 2010] He answered his question this way:
“Perhaps, and there is plenty of literature on how to manage such risks, which includes keeping your fingers crossed and doing nothing. Doing nothing (or not much more than what you’re doing today) might be a justifiable decision, but it’s a decision that has to be reached after your supply chain team and corporate executives have thoroughly analyzed and discussed this risk. The goal is to avoid asking, sometime down the road, how you could have been so complacent for so long.”
Kit Merker, a Microsoft employee, who writes about preventing and preparing for software disasters on www.softwaredisastersblog.com, wrote an interesting article for Manufacturing Net that raises a number of questions you should ask when preparing to prevent or mitigate an IT crisis. [“What You Wish You Knew During A Crisis,” 24 February 2012] Although Merker’s questions are aimed at IT departments, other departments would be smart to answer them as well. Merker writes:
“During a crisis, there is almost by definition a shortage of accessible information. Because of the time pressure a disaster creates, anything considered noise gets filtered out and ignored. However, if you could create a plan to track the right information and make it available during difficult times, it could mean the difference between tragedy and a close call. Creating and maintaining information repositories that can be used in a crisis is not necessarily cheap or easy, and you have to make a call about the ROI of this type of tool. If you’re responsible for disaster & continuity planning, you will need to make the case for why the organization should take on the burden of additional systems.”
Merker’s first question involves taking stock of where you are and how you have handled past crises. He writes:
“How Did We Handle This Last Time? If you’ve encountered the same or a similar problem before, it would be great to know what you did and who did it. Understanding how long it took might also help you set expectations with customers. Taking the extra time to record a few key pieces of information whenever you solve a production problem will help ensure that you can resolve similar issues in the future with speed & ease.”
Hopefully, your company has a crisis recovery and business continuity plan that incorporates lessons from the past. If your company doesn’t have one, there is no better time to start thinking about getting one. As Merker implies, lessons that are not documented are lessons that are not learned. His next question involves identifying stakeholders. He writes:
“Who Else Is This Affecting? Understanding the scope of impact of a particular symptom is a key to determining root cause. If your website is suddenly unreachable, you need to know if it is only related to you or to some portion of the Internet in general. Sometimes you can determine this with a simple test: Go to a high-availability website like www.yahoo.com. Other systems will likely need something more sophisticated. Ideally you can build this into your health and monitoring systems so your alerts can be intelligent.”
When it comes to mitigating supply chain disruptions, identifying end-to-end stakeholders is obviously important. A supplier’s supplier can have a significant impact on your operations and it can have serious consequences for your customer’s customer as well. So any good crisis management plan will ask, “Who else is this affecting.” Merker’s next question involves corporate reputation and social media buzz. He writes:
“What Are People Saying About Us? Listening to what customers are saying is critical during a crisis. Ideally, you will know about problems before they do, but that might not be the case depending on what the issue is and where you are in the crisis lifecycle. Creating a place for people to raise issues easily is a great way to learn about issues early and respond to them quickly. You can also set up alerts for news feeds, blog posts and twitter terms so you can see if people are talking about you, which might indicate that something is out of the ordinary. There are a variety of complaint sites out there (RipoffReport.com and Complaints.com, for example) where people can go and talk about how terrible you are. Monitoring these should give you insights if you have systemic service issues, some of which may be caused by systems instability or disaster response. And, of course, never just delete negative comments!”
Since technology providers never really know exactly how people are going to use a technology once it’s in someone else’s hands, they really can’t anticipate all the problems (or opportunities) that may arise. Monitoring social chatter is good way to stay on top of things before they actually become a crisis. Merker’s next question involves communication and information sharing. He writes:
“What Should I Tell People? When you suddenly realize that you caused a problem for your customers and you’re not sure how to fix it, this is not the time to figure out how to tell them. At the same time, you can’t predict what problems will be encountered and create prepared messages for all of them ahead of time. Communication policies will guide your team to a clear message. Set some principles and goals about the tone, level of detail, channels and frequency of updates, both for internal and external audiences. Providing customers and employees with clear updates is key to gaining respect and a positive reputation during a crisis. A simple way to think about this communication is Regret, Reason, Remedy. For a great example of this, look at how wordpress.com handles its downtime. There are other great examples and ideas on mashable.”
It’s never easy to admit you made a mistake (whether you’re a business or an individual); nevertheless, I believe Merker’s “man up” policy is the right one. That’s true for almost everyone, not just business people. I can think of a number of politicians who probably wish they would have “come clean” rather than trying to hide missteps they made. Once you’ve demonstrated that you are neither honest nor reliable you may never be able to regain the kind of trust that is needed to succeed with your customers. Merker’s next question really gets to the heart of the information you need to respond to a crisis. He asks:
“What Data Have We Lost? Figuring out what data has either been disclosed or is unrecoverable is very tricky. In the case of a disclosure attack, it may be impossible to ever learn what was lost. In that case, you have to take a pessimistic view.”
Without knowing the extent of the crisis, you can’t provide good information to other affected stakeholders. A good risk management framework should have viable troubleshooting and assessment processes built in — which is exactly what Merker’s final question addresses. He asks:
“How Can You Get This Information? You have two key types of information that you need to track in order to be ready for a crisis: internal and external. Internal information tells you what you’ve done before, who can help with what kinds of problems, what options and rules exist internally for a crisis, and what is happening right now. External data has to be collected from the outside world and made sense of in order to be useful. You can create direct channels of information: user communities, blogs, forums, or support tickets. You can also look at indirect information: Twitter topics and hash tags, third party review sites, blog posts and articles. There are a variety of systems you could use to store your info, but the important step is to get it into a well known location, filtered to only the most critical and valuable information and organized logically. Once you start collecting information and making it available, you risk having so much that it’s unwieldy.”
Merker concludes, “It’s hard to have the right information to make fast and accurate decisions in the heat of a crisis. But if you build the right systems, you may be able to get better early warnings and responses in place to turn down the heat on your next disaster.” A Chinese analyst by the name of Yingchun Guo agrees with Merker that you must build knowledge into your risk management processes. [“Research on Knowledge-Oriented Supply Chain Risk Management System Model,” Journal of Management and Strategy, Vol. 2, No. 2, June 2011] Guo writes:
“Supply chain risk management is a process of combining theoretical knowledge, practical experiences, tools, and methods together. The application of knowledge-oriented SCRM should emphasize on the knowledge of daily logistics, systematically mining, storing, and transforming the explicit knowledge and tacit knowledge accumulated in the process of risk management practice. Meanwhile, it is necessary to absorb ordinary external knowledge and learn best practices from others, providing managers with explicit knowledge in the form of information materials and assisting tools, and providing them with tacit knowledge in the form of cases.”
Commenting on Guo’s work, Daniel Dumke notes that Guo “sees several key elements to improve SCRM by using available knowledge within the chain.” [“Knowledge based Supply Chain Risk Management,” Supply Chain Risk Management, 19 September 2011] Those elements are:
- “Usage and sharing of the knowledge about supply chain risks: In supply chain risk management it is necessary not only to know about the company’s own risks but also include the knowledge about the risks of other supply chain participants.
- “This knowledge sharing should be supported by information technology.
- “A dynamic knowledge alliance should build the organizational foundation, members are dynamically selected due to their importance in the chain.
- “Positive effects of the knowledge based SCRM do not come instantly so, long term cooperation will be needed.
Guo published the following figure to show how he thinks a knowledge-oriented supply chain risk management framework should be built.
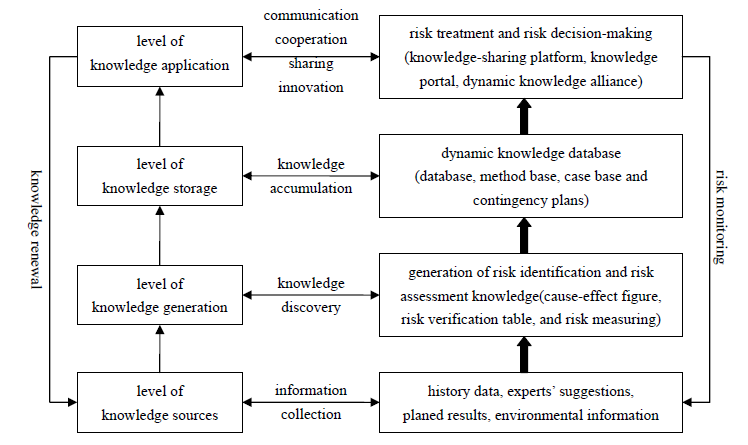
Referring to this figure, Dumke writes:
“The author recommends [basing] implementation on a) the accumulation of risk knowledge, emphasizing the importance of building the database and filling it with relevant data and furthermore b) developing a dynamic knowledge alliance. Primarily this alliance also signifies an organizational shift towards a more open exchange between companies, for [these] processes for risk gathering, storage, etc. have to be standardized across companies.”
Integration of data is probably more important than standardization across companies. Standardization may be a goal beyond most companies’ reach. The real bottom line is that supply chain risk management is improved when data is turned into actionable knowledge. By asking, what information would I really like to have available during a crisis, and figuring out how you can make it available, you dramatically improve your chances of being better prepared should (or should I say when) a crisis emerge.




