Today’s post was written by Dr. Ken J. Brumfield, a senior management consultant and professor, who has recently published a book about the relationship between organizational culture and crises. I’ll provide a short review of that book following Dr. Brumfield’s article. He writes:
Risk is defined as anything that may disrupt the day-to-day activities of an organization or prevent planned activities, processes, or events from occurring. Risk management is “the total process of identifying, controlling, and eliminating or minimizing uncertain events that may affect system resources” (Kovacich, 2003, p. 50). Many companies rely on a particular senior executive, often appropriately named the chief risk officer, to be aware of the various risks the organization may face and to comprehend their potential to affect the organization. Ultimately, however, the entire top management team is responsible for creating an integrated supply chain risk-aware culture. This includes understanding how their culture affects their managers’ decisions during supply chain crisis management.
As a component of their strategic planning duties, top management teams must create and maintain an integrative supply chain risk management framework. For instance, top management teams within technology organizations responsible for risk management in the area of information technology would find the National Institute of Standards and Technology (NIST) 800-30 document helpful for integrating supply chain risk management. NIST developed the 800-30 document to assist organizations engaged in information technology-related activities protect against and mitigate information technology risks. NIST 800-30 is used across departmental functions within companies and agencies. “The assessment is broad in scope and evaluates security vulnerabilities affecting confidentiality, integrity, and availability. The assessment recommends appropriate security safeguards, permitting management to make knowledge-based decisions about security-related initiatives” (CDC, 2007, pg. 2). The NIST 800-30 provides qualitative data to assist management with making decisions that provide efficient and effective security against internal and external information technology threats and would be particularly helpful for mitigating risks associated with supply chain management at a technology company or engaged in technology related operations.
According to the Centers for Disease Control, NIST 800-30 covers several different types of information technology controls. The first is management controls and it encompasses a company or organization’s information technology infrastructure, information technology risks, and the company’s information technology risk appetite. The second is operational controls and this area covers all of information technology related security matters involving human resources, “including all aspects of physical security, media safeguards, and inventory controls” (CDC, 2007, pg. 2). The third is technical controls and these controls consist of hardware and software security protections for systems throughout the company.
NIST 800-30 Risk Assessment Process and Benefits
The NIST 800-30 assessment consists of several different phases. Before describing the first phase of the assessment, it is important to understand the value it adds for management personnel such as the Chief Information Officer or other top management personnel responsible for technology operations (CDC, 2007, pg. 2). The first phase is the pre-assessment phase. This phase “begins with a process of data collection and network reconnaissance to learn as much as possible about the network topology and its hosts.” Several components are involved in this process and it consists of the Questionnaire and On-site phase. Team members ask questions of site-based management teams about the “physical, environmental, operational security of the IT system” (NIST 800-30, 2002, pg. 12). This would be very helpful in assisting companies with their current threat assessment capabilities and positioning them to start the mitigation process.
Next, the Document Review phase consists of a team tasked with reviewing a range of documents including policy manuals, security processes, security assessment, risk-management reports, etc. Automated scanning tools are used because “a network mapping tool can identify the services that run on a large group of hosts and provide a quick way of building individual profiles of the target IT system(s)” (NIST 800-30, 2002, pg. 12). During this phase agencies such as the Centers for Disease Control have created sophisticated best practices and instituted a template to mitigate risks. At the CDC, “the Business Steward is responsible for formally accepting each recommended control or rejecting it and providing an alternative” (CDC, 2007, pg. 3).
The next phase is the actual Assessment phase. A component of this phase is the Threat-Source Identification process that identifies threats to critical company operations. Threats are “defined as any circumstance or event with the potential to cause harm” to critical processes (NIST 800-30, 2002, pg.12). Another component, Motivation and Threat Actions considers the human threats that present themselves against the company’s interests. In this step, the CDC focused on system wide vulnerabilities that could be potentially exploited by both internal and external threat sources. System Security Testing “can be used to identify system vulnerabilities efficiently, depending on the criticality of the IT system and available resources (e.g., allocated funds, available technology, persons with the expertise to conduct the test)” (NIST 800-30, 2002, pg. 13).
NIST 800-30 suggests three phases of testing for IT threats, which are: automated vulnerability scanning tool, Security Test and Evaluation (ST&E), and Penetration Testing. The last phase is the Post-Assessment phase whereby senior management and other essential officials participate in following the recommendations discovered during the risk mitigation process. “Because the elimination of all risk is usually impractical, senior management and business stewards should assess control recommendations, determine the acceptable level of residual risk, and implement those mitigations with the most appropriate, effective, and highest payback” (CDC, 2007, pg. 6).
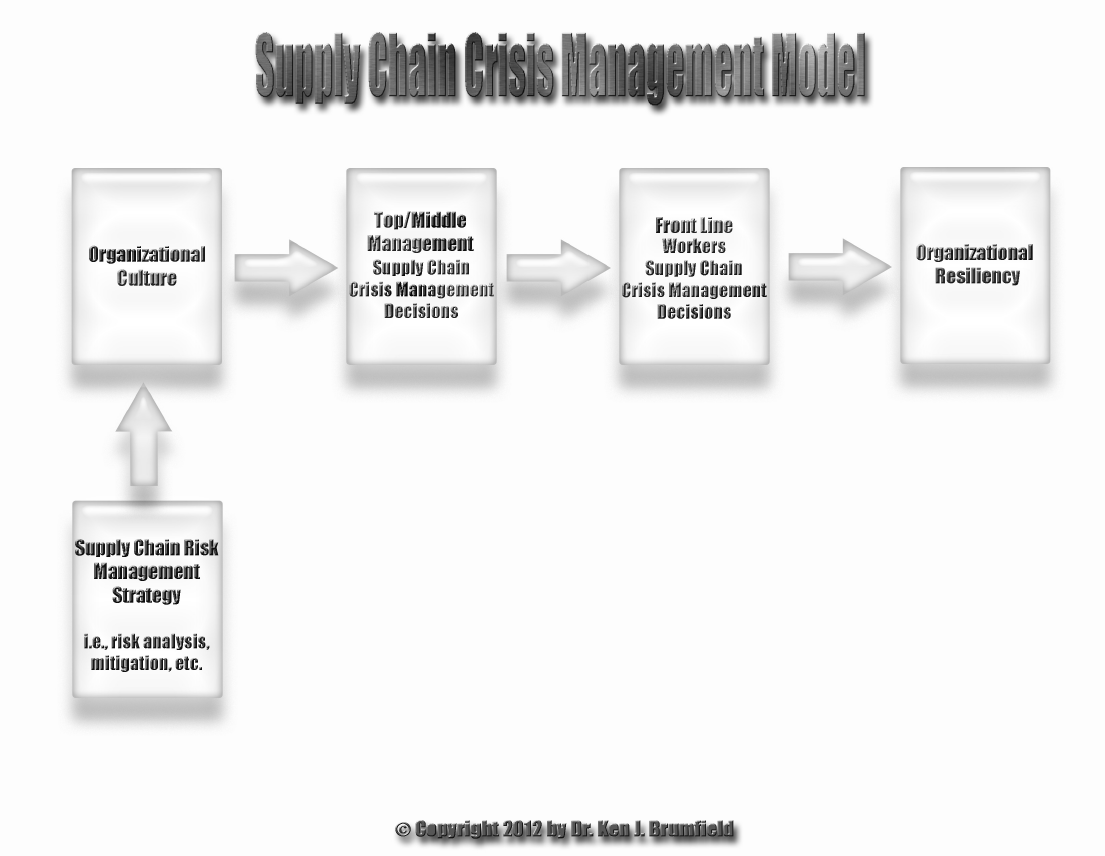
During strategic planning, if top leaders create and maintain an integrated supply chain risk management framework that includes strategic planning tools such as the NIST 800-30 document, mid-level managers will be more likely to provide cultural attributes that support successful crisis outcomes. Top management teams that use a risk management framework in their strategic planning also realize the following organizational benefits in mitigating risks: 1) an integrated supply chain risk management culture is embedded throughout the entire organization based on upper management prioritization of risk management and 2) policies, risk metrics and reports, and early warning indicators may be developed to complement the risk management initiatives. The Supply Chain Crisis Management Model below illustrates when a supply chain risk management’s framework is embedded in an organization’s culture. It subsequently shows the top management team’s culture infused with this same supply chain risk management culture. Consequently, the top management team’s underlying supply chain risk management values are passed onto the middle management team at a particular company and the middle management team’s supply chain risk management culture is passed onto the company’s front line workers. As a result of this prevailing organizational supply chain risk management culture dominating every layer within the organization’s structure, the organization is likely to experience organizational resiliency due to successfully managing it supply chain management during a crisis.
References:
Centers for Disease Control and Prevention (2007). Draft Risk Assessment Report. Atlanta.
Feringa, A., Goguen, A., and Stoneburner, G. (2002). National Institute of Standards and Technology-Risk Management Guide for Information Technology Systems (Special Publication 800-30). Retrieved February 26, 2011, from csrc.nist.gov/publications/nistpubs/800-30/sp800-30.pdf.
Kovacich, G. (2003). Information systems security officer’s guide: Establishing and managing an information protection program. Burlington, MA: Elsevier.
_________________________________________________________________
As noted in the introduction, Dr. Brumfield is author of a new book entitled S.E.T. Culture: What Every Organization Needs to Know before Crises Occur. In the book, he discusses the importance of Senior Executive Teams (SETs) when it comes to ensuring that organizations are prepared to face and overcome crises. Brumfield writes:
“The SET is the highest management level within an organization. These leaders have responsibility for the day-to-day operations and, ultimately, the profitability of their company. … The specific titles that comprise the SET may vary based on the type and size of the organization.”
In past posts, I have noted the importance of culture in helping make an organization successful. Brumfield insists that the SET is the most critical group when it comes to ensuring that the right culture is fostered and maintained. When a crisis occurs, culture and training must combine if an organization is going to survive. Brumfield writes, “When crises occur at the organizational level, any number of critical disruptions may occur. Companies may lose financial resources and key personnel. Infrastructure may break down. Continuation of normal operations may even be impossible.” If the SET has performed its role correctly, organizational instincts will take over during a crisis and the organization will rise to successfully handle emerging challenges.
Brumfield asserts that “understanding the SET culture of an organization is the key to understanding and determining how mid-level managers will perform in crisis events.” He is not the first analyst to identify the important role that mid-managers play in an organization; but, he is the first academic in a long time to reiterate that role. During the 1990s, the ranks of mid-level managers were decimated as companies tightened their belts in order to increase profits. Brumfield writes:
“The culture affects the way these mid-level managers make decisions. Because mid-level managers play critical, even pivotal, roles during crisis events, their decisions affect the success or failure of their organizations in surviving the crisis.”
Brumfield’s book is short (less than 70 pages), but it is filled with examples and sound advice. Waiting until a crisis occurs to try and figure out how your organization should respond is too late. Brumfield’s book can help you establish the kind of organizational culture your organization will need to withstand the pressures created when a crisis occurs.




